NIS 2: The new EU Rules on Cyber Security Explained
NIS2 obliges companies to improve their cyber security. Who is affected, what needs to be done - and why Swiss companies should also react.
5
min read
Aktualisiert am
August 5, 2025

The European Union is implementing stricter rules on cyber security. Hundreds of thousands of companies are affected. And not just them: Partner companies and supply chains are also to become more secure. We present the new EU cyber security regulation "NIS2" and take a look at everything you need to know about reporting obligations and co.
The EU has launched a directive "for a high common level of cybersecurity". Officially known as "Directive (EU) 2022/2555" or "NIS2" for short, it is the second attempt to increase network and information security and thus strengthen cyber resilience. Since October 17, 2024, EU member states have had to transpose the directive into national law. In many countries - including Belgium, Denmark and Italy - this has now happened. In other countries, full implementation is delayed; in Germany, for example, the NIS2 Implementation Act (NIS2UMSuCG) is planned and is to be submitted to the Federal Council for its opinion in late summer 2025. It is relevant for Switzerland because the directive explicitly includes supply chains and partner companies.
Which companies are affected?
The new directive affects around ten times more businesses than its predecessor from 2016. According to current estimates, around 160,000 companies are affected across Europe. In Germany alone, the number is now estimated at around 30,000.
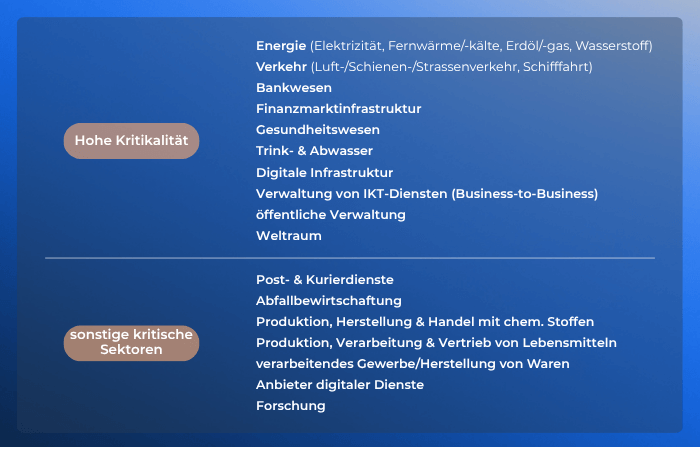
For example, NIS 2 has increased the list of sectors from eight to 18. They are categorized as "essential" and "important". A detailed overview can be found in Annexes I and II of the directive linked above.
The energy, transport, banking, financial market infrastructure, healthcare, drinking water, wastewater, digital infrastructure, management of ICT services (B2B), public administration and space sectors are therefore particularly important.
The list of "other" critical sectors includes postal and courier services, waste management, production, manufacture and trade in chemicals, production, processing and distribution of foodstuffs, manufacturing/production of goods and providers of digital services.
As a general rule, companies in these sectors are affected if they employ more than 50 people and have an annual turnover or annual balance sheet of more than 10 million euros. However, exceptions are possible, particularly if a company is the sole provider of an essential service in a member state or is of particular relevance to national security.
What do the NIS2 requirements include?
The obligations can be found in Chapter IV of the Directive. According to Article 21, affected companies should "take appropriate and proportionate technical, operational and organizational measures to manage the risks to the security of network and information systems (...) and to prevent or minimize the impact of security incidents on the recipients of their services and on other services." What is considered "proportionate" should be based, among other things, on the assessed risk, the possible consequences and the size of the operation.
Article 21 also lists a minimum standard for security measures. These include a concept for risk analysis, plans for dealing with security incidents, crisis and backup management, concepts for evaluating the effectiveness of measures, encryption, access control and multi-factor authentication.
Swiss companies that follow the ICT minimum standard are already well positioned here.
Article 21, paragraph 2, also explicitly mentions: "security of the supply chain, including security-related aspects of the relationships between individual entities and their direct suppliers or service providers". Paragraph 3 states that entities must consider "the overall quality of the products and cybersecurity practices of their vendors and service providers, including the security of their development processes".
What does the NIS2 security incident reporting obligation cover?
The newly introduced reporting obligation in Article 23 is also particularly relevant: in the event of a security incident, an early warning must be issued within 24 hours of becoming aware of it. This is followed within 72 hours by a more detailed report with an initial assessment of the security incident, including its severity and impact. A follow-up or final report with a root cause analysis and countermeasures must be submitted to the competent authority after one month at the latest.
Violations of the reporting or security requirements can be punished with high fines: For particularly important institutions, fines of up to 10 million euros or 2 percent of annual global turnover can be imposed - whichever is higher. The implementation of the requirements is monitored in the member states by the responsible authorities (e.g. the BSI in Germany).
The explicit responsibility of management is also new: CEOs, CIOs and board members must ensure that the required measures are not only introduced, but also understood and monitored. Many national laws require mandatory training and the possibility of personal liability.
Why these new rules?
It is not only since yesterday that EU policy has recognized that increasing digitalization and networking also represent a potential threat. However, previous attempts to comprehensively raise security standards have not been particularly successful.
The direct predecessor of the new regulations is Directive (EU) 2016/1148, which already had the same thrust, but its implementation in the member states was hardly monitored and in many places it was less specific than the new version.
In the meantime, even more processes have been digitized, automated and networked. At the same time, the number of attempted and successful attacks on networks of industrial plants and public institutions has increased.
With NIS2, the EU is responding to this threat situation and ensuring greater commitment and harmonization - also in order to avoid a fragmented level of cybersecurity within Europe. The directive is also part of a larger package on the resilience of critical infrastructures.
Closing words
The new EU directive largely follows what is already recommended and practiced internationally. In Switzerland, there are comparable guidelines, such as the National Cyber Security Center (NCSC) and the ICT minimum standard for public authorities. In addition, a revision of the Information Security Act (ISG) is underway, the content of which is strongly based on NIS2.
However, it is a good idea for businesses of all kinds to be aware of potential threats and their consequences, even if they are not considered part of the "critical infrastructure". Cyberattacks such as ransomware attacks can cause considerable monetary damage and ruin a company's reputation.
FAQ: The NIS2 at a glance
What is the NIS2 directive?
EU Directive 2022/2555 (NIS2) is the revised EU regulation on the cybersecurity of critical and important facilities. It replaces the NIS1 Directive from 2016 and massively expands its scope. It pursues the goal of a uniformly high level of cybersecurity in the EU in accordance with Art. 1 NIS.
Which companies are affected by NIS2?
All companies from sectors with high criticality and other critical sectors with more than 50 employees and more than 10 million turnover or balance sheet total, as well as systemically important smaller providers.
What does NIS2 actually require?
NIS2 requires technical and organizational security measures, risk analysis, emergency plans, training, security incident reports and management responsibility.
Are there sanctions for violations of NIS2?
Yes, violations of NIS2 are sanctioned. Fines of up to 10 million euros or 2% of annual global turnover may be imposed. Management can also be held liable.
Does the NIS2 Directive also apply to Swiss companies?
Although Switzerland is not an EU member state, NIS2 may also have an impact here - particularly on companies that have subsidiaries or customers in the EU or are active as service providers in EU supply chains.
More knowledge that takes you further
Discover relevant insights on current topics, challenges and solutions that will help you move forward.